The Purdue Model
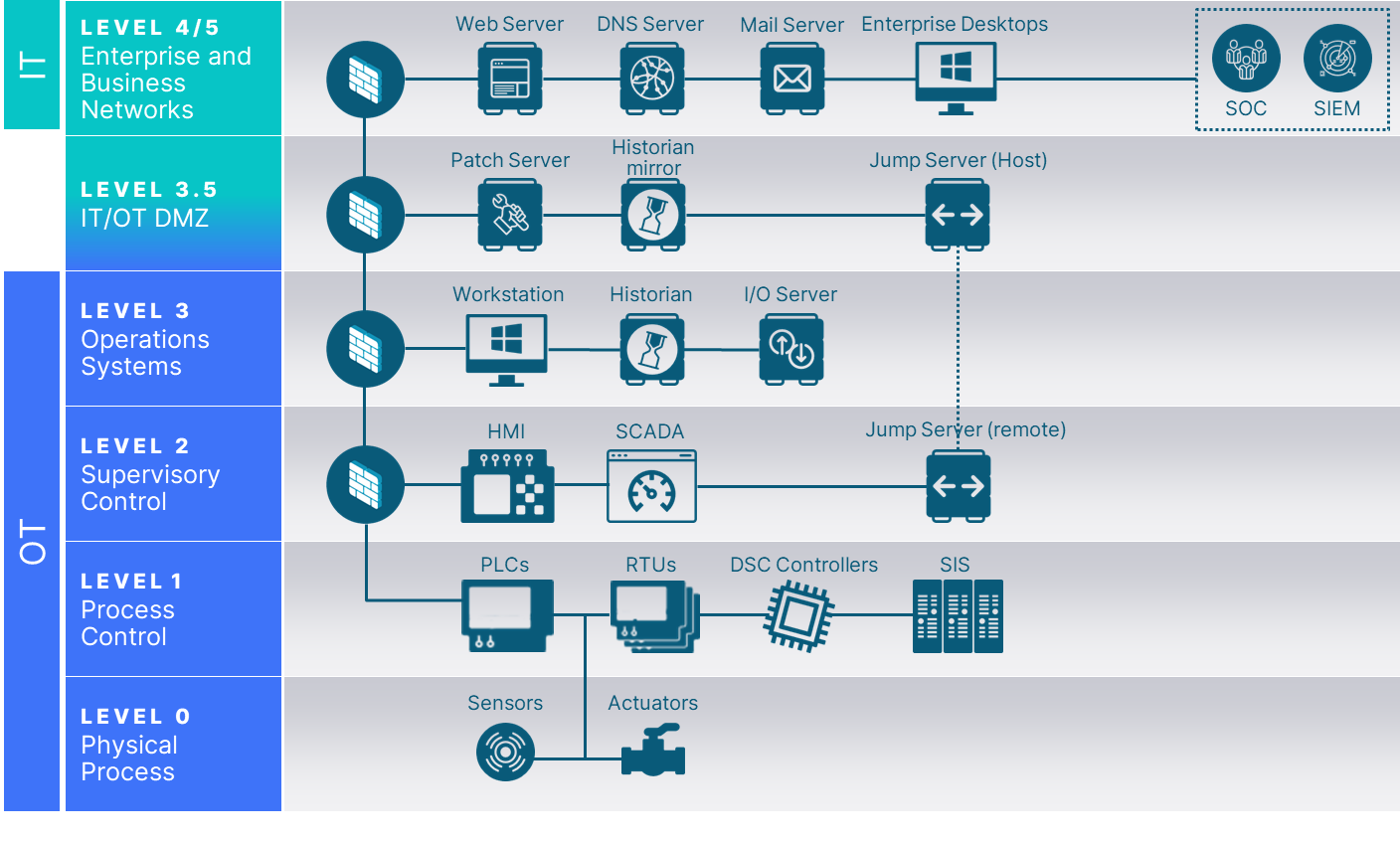
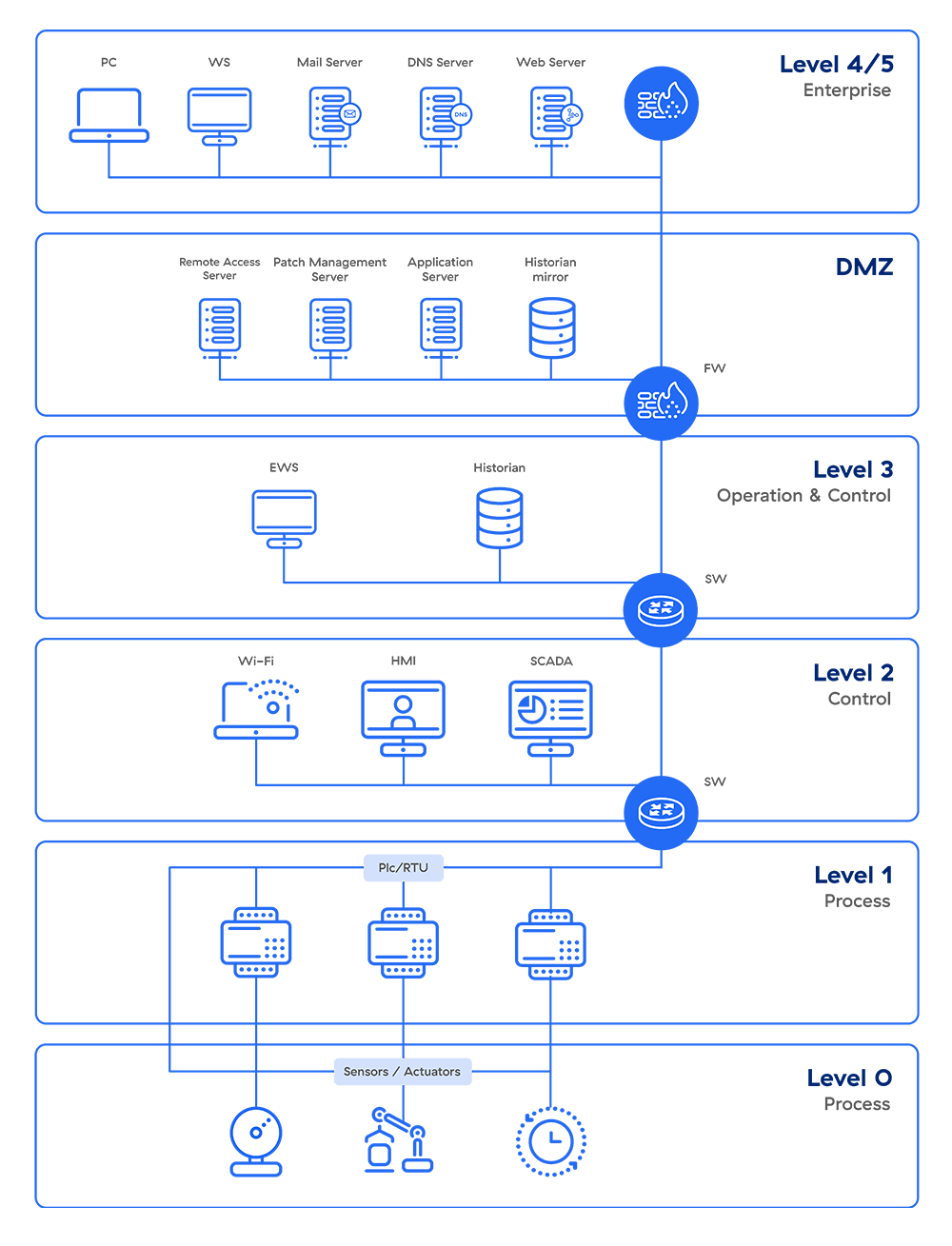
The Purdue model is generally accepted as the standard for building an industrial control system (ICS) network architecture in a way that supports OT security, separating the layers of the network to maintain a hierarchical flow of data between them, and as such, reflects the baseline architecture requirements for many industrial control system frameworks such as API 1164, ISA/IEC 62443, and NIST 800-82.
The Purdue model, part of the Purdue Enterprise Reference Architecture (PERA), was designed as a reference model for data flows in computer-integrated manufacturing (CIM), where a plant’s processes are completely automated. It came to define the standard for building an ICS network architecture in a way that supports OT security, separating the layers of the network to maintain a hierarchical flow of data between them.
OT security is the measures and controls in place to protect OT systems—which use purpose-built software to automate industrial processes—against cybersecurity threats. As the convergence of information technology and OT drives greater automation and efficiency in industrial systems, OT security has become a requirement of critical infrastructure management.
What Are Industrial Control Systems?
At its core, an ICS is like an orchestra conductor, ensuring that all instruments play in harmony. ICS is a broad term, including hardware, software, and networks that monitor and control industrial processes and machinery. These processes span sectors such as energy, manufacturing, water treatment, transportation, etc. Imagine a power plant adjusting its operations to meet fluctuating electricity demand or an assembly line producing cars with precision, all thanks to ICS.
The Importance of ICS in Critical Infrastructure
The ICS are the unseen pillars supporting the critical infrastructure that sustains our modern society. They manage and control essential services that we often take for granted. Think of the water that flows from your tap, the lights that come on when you flip a switch, or the fuel that powers your vehicle—ICS makes these everyday conveniences possible. Moreover, they play a crucial role in ensuring the reliability, efficiency, and safety of these services.
- Level 4/5: Enterprise Zone
- The topmost zone in the Purdue Model is the Enterprise Zone. This zone encompasses the typical IT network where primary business functions occur, such as manufacturing operations orchestration.
- 2. Level 3.5: Demilitarized Zone (DMZ)
- Sitting between the IT and OT zones, the Demilitarized Zone (DMZ) serves as a buffer or convergence layer. It comprises security systems like firewalls and proxies, which prevent lateral threat movement between IT and OT environments.
- 3. Level 3: Manufacturing Operations Systems Zone
The Manufacturing Operations Systems Zone is where customized OT devices reside, managing production workflows on the shop floor. This zone includes various components:- Manufacturing Operations Management (MOM) systems, which oversee production operations.
- Manufacturing Execution Systems (MES), which collect real-time data to optimize production.
- Data historians, which store process data and perform contextual analysis in modern solutions.
Disruptions in this zone can lead to economic damage, critical infrastructure failure, risks to personnel and plant safety, and revenue loss.
- Level 2: Control Systems Zone
- The Control Systems Zone encompasses systems responsible for supervising, monitoring, and controlling physical processes within the ICS network. Key components in this zone include:
- Supervisory Control and Data Acquisition (SCADA) software, which oversees and controls physical processes, locally or remotely, and aggregates data for historians.
- Distributed Control Systems (DCS), which perform SCADA functions and are typically deployed locally.
- Human-Machine Interfaces (HMIs), connecting to DCS and Programmable Logic Controllers (PLCs) to enable basic controls and monitoring.
- The Control Systems Zone encompasses systems responsible for supervising, monitoring, and controlling physical processes within the ICS network. Key components in this zone include:
- Level 1: Intelligent Devices Zone
- The Intelligent Devices Zone consists of instruments that send commands to devices at Level 0. Key components in this zone include:
- Programmable Logic Controllers (PLCs), responsible for monitoring automated or human inputs in industrial processes and making corresponding output adjustments.
- Remote Terminal Units (RTUs), connecting hardware in Level 0 to systems in Level 2.
- The Intelligent Devices Zone consists of instruments that send commands to devices at Level 0. Key components in this zone include:
- Level 0: Physical Process Zone
- At the lowest level of the Purdue Model, the Physical Process Zone comprises sensors, actuators, and other machinery directly involved in assembly, lubrication, and other physical processes. Modern sensors in this zone communicate directly with monitoring software in the cloud through cellular networks.
Digital Transformation Changed Everything
Things changed with digital transformation, and the assumptions that underpinned the Purdue Model no longer apply. Where hierarchical network communications (between layers) were once the norm, hyper-convergence now dominates. Systems and devices can just as easily communicate across layers within the enterprise and to the cloud as they can to other organizations across a global supply chain. Today, the boundaries that once separated OT and IT have blurred in favor of achieving greater operational efficiency.
Those gains come with risk. Because of this convergence, attacks that are common to IT and IoT systems in the “carpeted realm” can now move laterally and, once inside the enterprise, reach OT assets in the manufacturing and operational realms. Similarly, the old assumption that industrial systems were the true “crown jewels” of the enterprise has given way to the understanding that any system or device can be mission-critical. An attack on billing systems or supply chain can cripple a manufacturing business as effectively as an attack on the factory infrastructure.
Unfortunately, the vulnerability of industrial and critical infrastructure has been made clear over the past year, and cybercriminals and threat actors are taking full advantage of the opportunity. The cyberattack on Colonial Pipeline, for example, showed that the means by which threat actors are able to compromise industrial systems have been via IT systems. In the Colonial Pipeline case, the IT system was compromised and that brought down operations even though OT was not impacted. Yes, operational technologies are vulnerable, but they are being attacked through IT networks. In fact, an examination of cyberattack statistics compiled from the IBM X-force 2020 Threat Intelligence Index and the Dragos Manufacturing Sector Threat Perspective 2020 reveals that most attacks affecting OT environments are garden variety cyberattacks, not SCADA/ICS attacks.
Segmentation Remains A Valid Concept
Implementing microsegmentation at the network level, ensuring that access controls are applied based on device attributes, risks, and OT protocols. By monitoring east-west communication, organizations can detect anomalies and apply granular security rules to control traffic across zones. One significant advantage of zero trust in ICS environments is the ability to provide secure remote access to ICS assets without the need for physical segmentation at each layer.
Visibility Across IT, IoT And OT
The first step toward that goal is by establishing comprehensive visibility into all devices in an enterprise’s technology infrastructure and then monitoring device behavior. This means visibility across the converged IT and OT environment. For example, in a modern, hyperconverged world, an attack on IT that takes down your billing system will impact your ability to operate, even if your OT and industrial infrastructure have not been impacted.
This is necessary to establish zero trust segmentation, which requires understanding each device’s “transactional flows,” or behavioral patterns. This is the ideal application for machine learning technology as devices have deterministic functions. Therefore, zero trust segmentation can be enabled to allow appropriate operations while limiting exposure.
Many ICS network owners hesitate to adopt zero trust. Concerns over downtime causing lost revenue, disrupting infrastructure, or even endangering people’s safety make industrial operators uncertain about potential tradeoffs in costs and complexity, even as zero trust remains the most effective strategy for securing modern networks.
In some cases as private cellular networks gain traction, enabling mobility and standardized technology, zero trust principles can be applied to ensure secure and reliable remote access to Industrial Internet of Things (IIoT) and OT devices.
- Monitoring east-west communication between ICS assets.
- Applying granular security rules to control traffic across zones based on device attributes, risks, and OT protocols.
- Creating security rules that ensure systems use only communication protocols they were designed to use and that are based on the dynamic grouping of devices.
- Only allow secure remote access to ICS assets and OT networks.
Sources :
- https://securitdata.ca/blog/the-significance-of-the-purdue-model-in-ics-security/
- https://www.zscaler.com/resources/security-terms-glossary/what-is-purdue-model-ics-security
- https://www.safebreach.com/blog/bringing-it-and-ot-security-together-bas-purdue/
- https://blackcell.io/purdue-model-for-industrial-control-systems-infographic/
- https://truefort.com/what-is-the-purdue-model-for-industrial-control-system-ics-security/
- https://sectrio.com/blog/purdue-model-for-ics-security/
- https://www.forbes.com/councils/forbestechcouncil/2022/01/18/a-reimagined-purdue-model-for-industrial-security-is-possible/https://claroty.com/blog/ics-security-the-purdue-model
- https://www.sans.org/blog/introduction-to-ics-security-part-2/
- https://www.energy.gov/sites/default/files/2022-10/Infra_Topic_Paper_4-14_FINAL.pdf
- https://www.fortinet.com/resources/cyberglossary/purdue-modelhttps://www.automationworld.com/factory/iiot/article/21132891/is-the-purdue-model-still-relevant